Enterprise Security Solutions
Commercial security systems are comprehensive solutions designed to protect businesses, organizations, and commercial properties from a range of threats, including theft, vandalism, unauthorized access, and other security breaches. These systems employ a combination of technologies and devices to create a robust security infrastructure. Key components of commercial security systems typically include alarm systems, access control, and video surveillance (CCTV).
True Protection is an award-winning commercial alarm company that has helped thousands of businesses stay protected & manage their business. As a Texas company, we currently have commercial security installation teams in Dallas / Fort Worth, Houston, San Antonio & Austin.
Call us today to start customizing a smart security system for your business today.

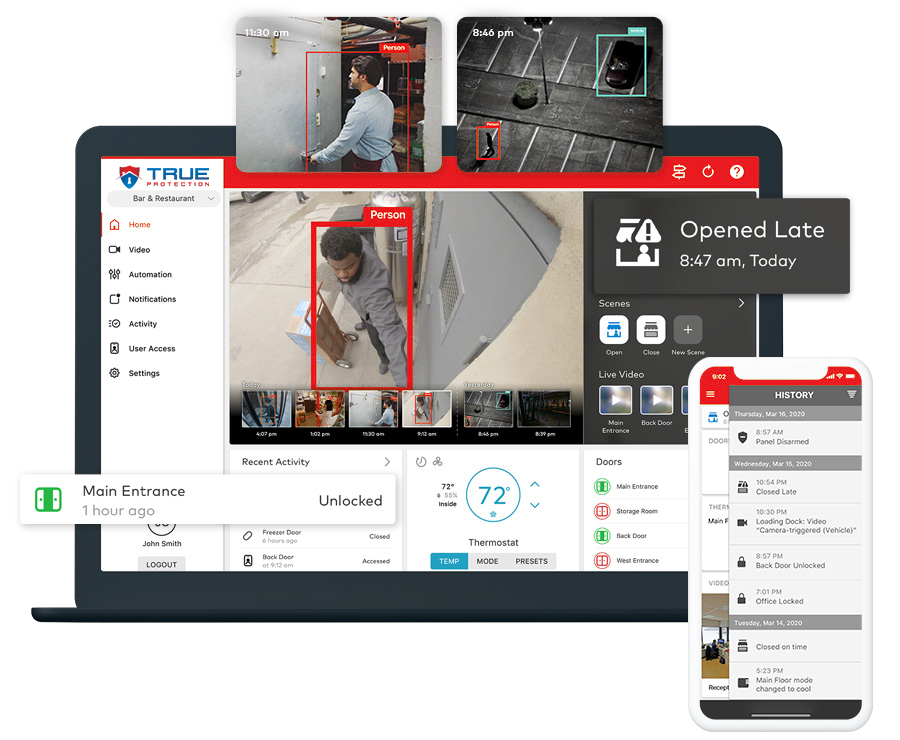
Keep an Eye on Multiple Locations
Take charge of your business’s security measures, energy consumption, access controls, and video surveillance systems across all your business locations.
- Check what’s happening at your properties in real time, sorted by security system status, opening/closing times, and access status.
- Group your locations together into areas or regions for easier management, instead of handling each location individually.
- Manage user codes, access permissions, and system settings for all locations at once, saving time and making sure everything is consistent.
- Keep all your locations safe with automatic software updates, secure encryption, and two-step verification.
- Set up scheduled reports that cover all your properties, giving you useful insights automatically.
Employees come to work late or leave early about 7.5 times per year, costing industrial business roughly $1,500 annually.1
1 Parks Associates, Alarm.com Medium and Large Commercial Business Survey 2021
Comprehensive Security Alarm Coverage
Connected commercial alarm systems offer a complete security solution, addressing various aspects of intrusion protection needs. Our systems integrate access control, video surveillance, intrusion detection, and fire protection into one platform, allowing for seamless monitoring and control.
Centralizing all security functions in a single system enables large businesses to effectively manage their security measures and promptly respond to any incidents.
Accurate and Real-time Operational Intelligence
Obtain vital multi-location data through daily, weekly, and monthly reports.
- Receive instant alerts if employees aren’t adhering to scheduled opening or closing times.
- Stay informed and gather proof of any activity in sensitive or off-limits zones.
- Utilize graphs showing peak business hours to guide staff scheduling and assess the effectiveness of promotional campaigns.

89% of business owners agree that integrating all their security features and making them accessible through one app is crucial.
Parks Associates, Alarm.com Medium and Large Commercial Business Survey 2021
Commercial Video Surveillance
With continuous on-site recording, cloud-based event storage, health monitoring, and smart analytics, your footage is always readily available when required.
- Automatically record and store videos of alarms and security system changes in safe, remote cloud servers.
- Smart detection analytics correctly identify individuals and vehicles entering your property, ignoring irrelevant movements such as shadows or rain.
- Get immediate notifications for unauthorized individuals or unexpected visitors in restricted areas or during non-working hours.
- Continuous real-time camera health monitoring guarantees your cameras are always functioning, recording, and providing clear views.

Powerful Video Analytics
Combining video surveillance with Artificial Intelligence (AI) can drastically enhance operational monitoring in various ways:
-
Automated Anomaly Detection: AI can be trained to recognize normal operational patterns and thus can identify anomalies or unusual activities.
-
Intelligent Video Analytics: AI algorithms can analyze video feeds in real-time to extract valuable information.
-
Predictive Analysis: By learning from historical video data, AI can help predict future events or behaviors, enabling businesses to anticipate potential issues before they occur.
-
Efficient Resource Allocation: By automating the monitoring process, businesses can free up human resources for tasks that require critical thinking and creativity.
-
Scalability: AI systems can manage vast amounts of video data from multiple cameras across different locations.

CALL +1-800-393-6461 NOW TO GET A FREE QUOTE.
Get protected with industry leading security, automation & service? Call now or fill out the form to get started.

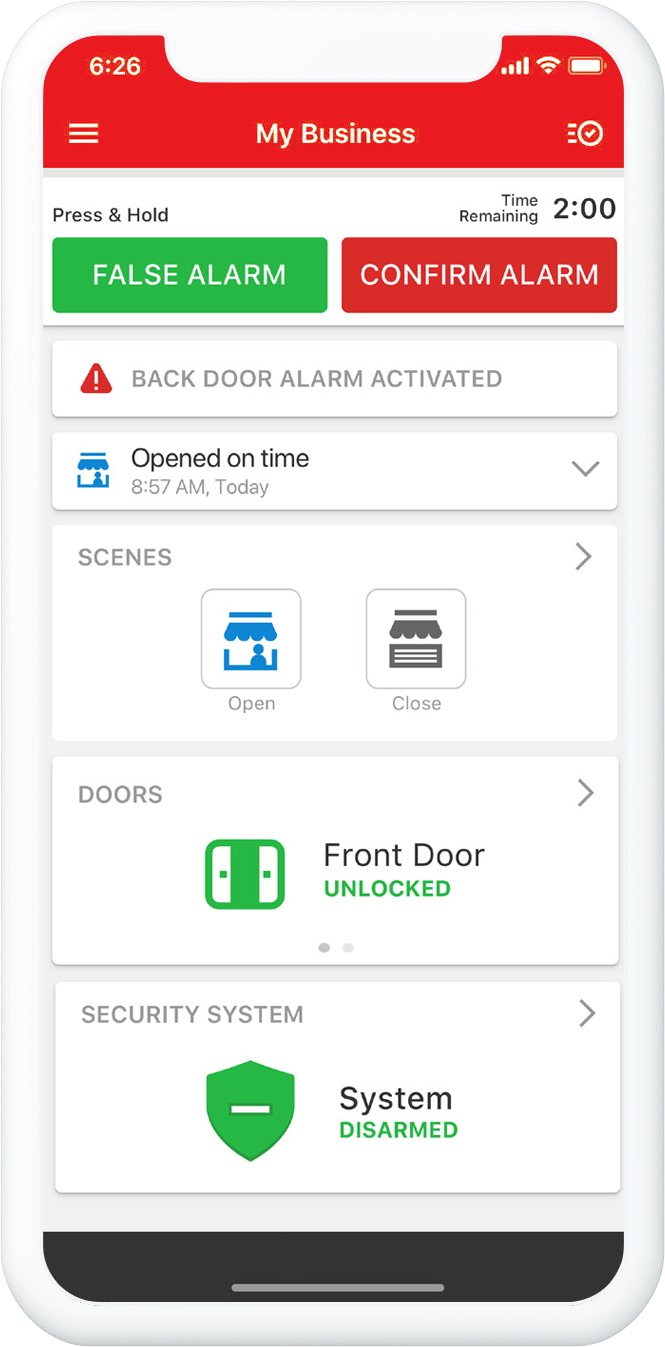
Enterprise Access Control
Smart security systems for businesses require access control systems for the protection of all types of business assets. Access control systems control people’s ability to access the physical location, including key cards, approved users, and door locking mechanisms.
There are a variety of access control systems, so each business will need to determine the best one for their needs. This depends on various things such as costs, hidden fees, maintenance needs, and the size of the enterprise.
Many organizations opt for on-site access control, however they can be difficult and costly to take care of and upgrade. True Protection helps with Cloud-based access control systems, ensuring ease of use and care, without on-site systems.
Access Control Software Security
Incorporate a user-friendly, cloud-based system with a scalable solution that perfectly blends alarm and video features.
- With our app or online dashboard, you can quickly add or remove access for users and cards. Our system allows for mass additions of users or automated deactivation of cards on specified dates, enhancing your efficiency.
- Our Mobile Credentials feature is a cost and time saver, enabling users to use their smartphones for building access.
- You can lock, unlock, and open doors remotely via your mobile app, providing convenience and flexibility. To minimize false alarms, our system disarms the intrusion panel automatically when the first person accesses a door.
- Access events and related video footage are immediately available in your access history timeline for easy reference and review.
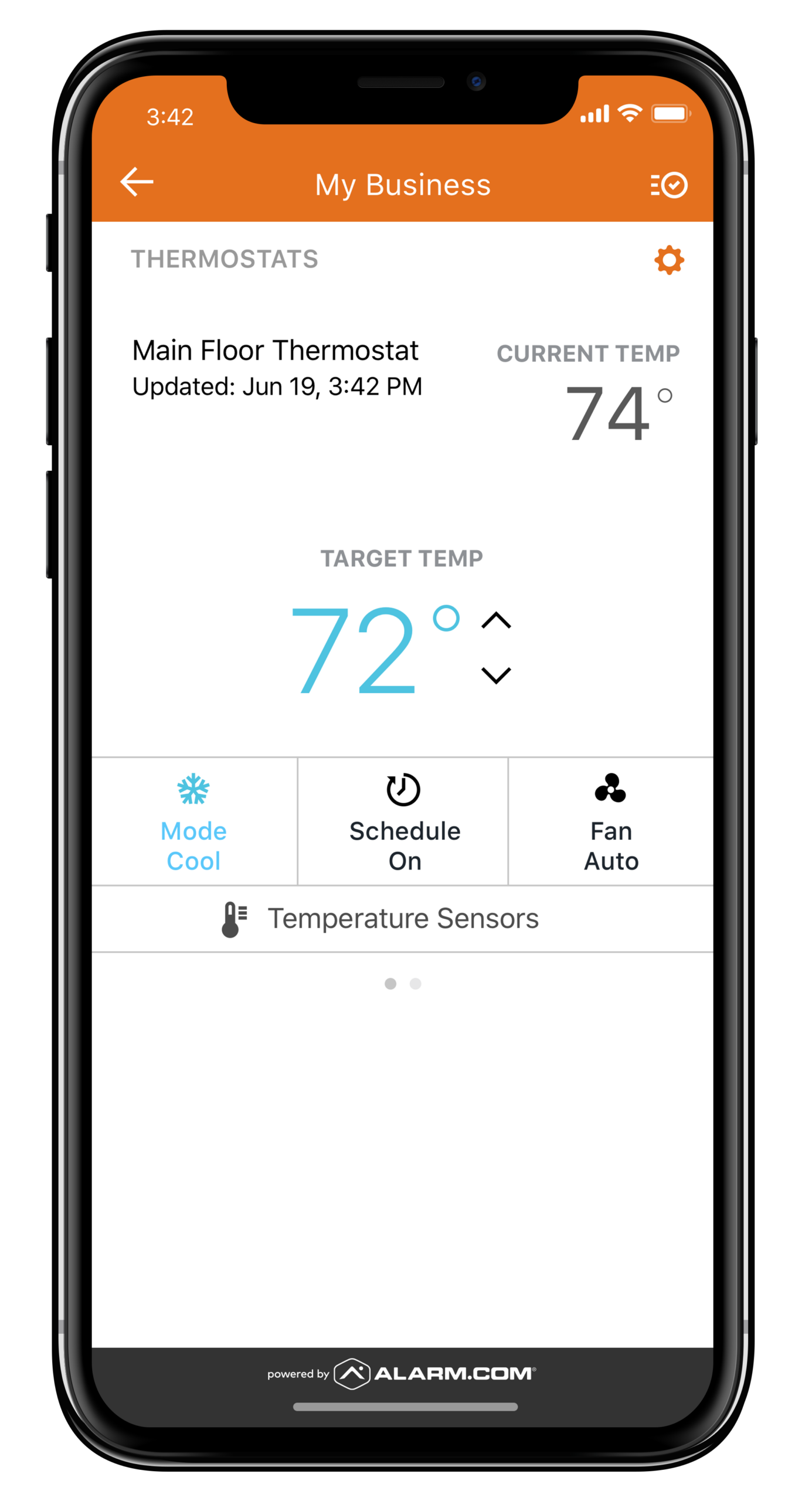
Business Energy Management Solutions
Sensors will inform you of fires or malfunctioning equipment such as refrigerators, freezers and HVAC systems. If you own a restaurant that carries a large inventory, equipment malfunctions can cost thousands of dollars and put your company at risk of serving spoiled food. However, the biggest ongoing benefit of smart systems is being able to control environmental functions with your phone.
Turn down the heat or air conditioning when the business is closed, or make adjustments as the temperature changes throughout the day. Control lights to reduce energy bills. Use remote controls to turn on the heat while getting ready for work so that the business is comfortable for customers when you open. The savings on utility bills alone often cover the costs of getting a good security system.
Tips for Effective Enterprise Security
Enterprise security is quite detailed and complex, however, it can be established easily with the help of a professional security company such as True Protection. We work with enterprises to implement effective security measures that also enable business growth.
Here are some tips for enterprise security:
- Identify weaknesses and areas of non-compliance with a security audit.
- Use enterprise specific access control.
- Make sure to meet compliance regulations.
- Use data protection and encryption.
- Streamline processes with automation.
- Ensure the entire team knows security measures and what to do in case of a data breach.
Commercial Security Installations in Texas
In Texas, we offer streamlined commercial security installations to safeguard your business. Our skilled team will assess your unique security needs and devise a personalized plan that suits your budget and objectives.
We integrate top-tier systems like access control, video surveillance, and intrusion detection, typically starting installation within 1-2 business days after finalizing your plan.
For a free evaluation and quote in Texas, fill out the form below or contact us.